Security Analysis
This tab is only available when the analysis profile of Security Analysis is selected. It includes six types of malicious activities.
Worm attack settings
The worm analysis detects suspicious worm
activities and the settings part appears as follows:
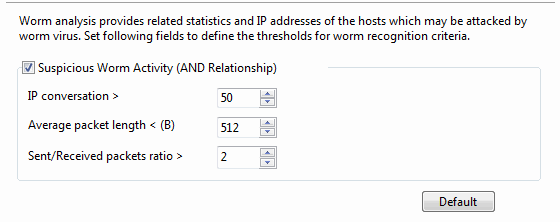
- Suspicious Worm Activity: Enables worm analysis, or else there will be no item to show on the Worm view. AND Relationship means the three conditions below should all be met to define the worm activity.
- IP conversation: Sets the IP conversation count of a host. If the IP conversation count of a host is greater than the setting value, it is supposed that the host may be attacked by worm virus. The value is an integer between 1 and 1,000, and 50 is set by default.
- Average packet length: The unit is byte. If the average packet length of a host is less than the setting value, it is supposed that the host may be attacked by worm virus. The value is an integer between 64 and 1,514, and 512 is set by default.
- Sent/Received packets ratio: The ratio of sent packets to received packets. If the ratio is greater than the setting value, it is supposed that the host may be attacked by worm virus. The value is an integer between 1 and 100, and 2 is set by default.
TCP Port Scan settings
The TCP port scan analysis detects the TCP port scanning activities and the settings part appears as follows:
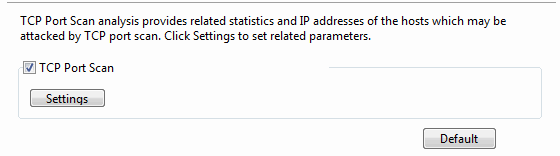
- TCP Port Scan: Enables TCP port scan analysis, or else there will be no item to show on the TCP Port Scan view.
- Settings: Locates to the TCP Port Scan diagnosis event on the Diagnosis tab. The count on the Event setting pane means the count of TCP port connected by a local or a remote host. If the count is greater than the setting value, it is supposed that the host is performing TCP port scan. The value is an integer between 5 and 50, and 6 is set by default.
ARP Attack settings
The ARP attack analysis detects ARP attack activities and the settings part appears as follows:
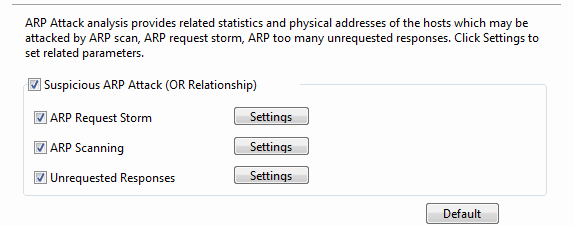
- Suspicious ARP Attack: Enables ARP attack analysis, or else there will be no item to show on the ARP Attack view. OR Relationship means one of the three conditions below is met to define the ARP attack activity.
- ARP Request Storm: Enables ARP request storm analysis. Click Settings to locate the ARP Request Storm diagnosis event on the Diagnosis tab. There are two main parameters for this event.
- Sampling Duration: The sampling time with the unit of second. The value is an integer between 1 and 3,600, and 20 is set by default.
- Request Times: The times of ARP Request. If the time is greater than the setting value in the sampling duration, it is supposed that there is ARP request storm attack on the network. The value is an integer between 1 and 10,000, and 10 is set by default.
- ARP Scanning: Enables ARP scanning analysis. Click Settings to locate the ARP Scanning diagnosis event on the Diagnosis tab. There are two main parameters for this event.
- Scan sampling duration: The sampling time with the unit of second. The value is an integer between 15 and 180, and 60 is set by default.
- No response packet percentage (%): The percentage of no response packets. If the percentage is greater than the setting value in the scan sampling duration, it is supposed that there is ARP scanning attack on the network. The value is an integer between 1 and 100, and 20 is set by default.
- Excessed active ARP response: Enables excessed active ARP response analysis. Click Settings to locate the ARP Too Many Active Response diagnosis event on the Diagnosis tab. There are two main parameters for this event.
- Unit Time: The sampling time with the unit of second. The value is an integer between 30 and 3,600, and 60 is set by default.
- Number of Sent Response: The number of sent response. If the number is greater than the setting value in the unit time, it is supposed that there is excessed active ARP response on the network. The value is an integer between 30 and 20,000, and 300 is set by default.
Suspicious Conversation settings
This function
detects the suspicious conversations of HTTP, FTP,
SMTP and POP3 and the settings part appears as follows:
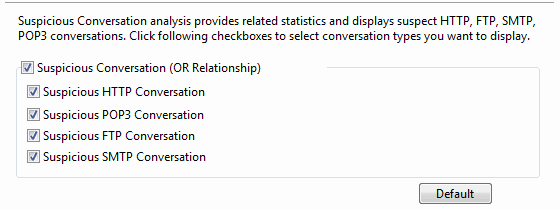
- Suspicious Conversation: Enables suspicious conversation analysis, or else there will be no item to show on the Suspicious Conversation view. OR Relationship means one of the four conditions below is met to define the suspicious conversation attack activity.
- Suspicious HTTP Conversation: Enables suspicious HTTP conversation analysis which is set by the program on the Diagnosis tab. It is supposed that there is suspicious HTTP conversation on the network when port 80 is connected without HTTP data.
- Suspicious POP3 Conversation: Enables suspicious POP3 conversation analysis which is set by the program on the Diagnosis tab. It is supposed that there is suspicious POP3 conversation on the network when port 110 is connected without POP3 data.
- Suspicious FTP Conversation: Enables suspicious FTP conversation analysis which is set by the program on the Diagnosis tab. It is supposed that there is suspicious FTP conversation on the network when port 21 is connected without FTP data.
- Suspicious SMTP Conversation: Enables suspicious SMTP conversation analysis which is set by the program on the Diagnosis tab. It is supposed that there is suspicious SMTP conversation on the network when port 25 is connected without SMTP data.
DoS Attacking settings
The DoS attacking analysis detects the hosts which perform DoS attack and the settings part appears as follows:
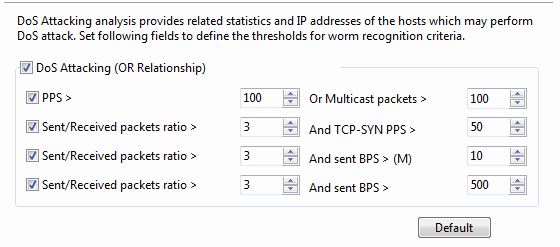
- DoS Attacking: Enables DoS attacking analysis, or else there will be no item to show on the DoS Attacking view. OR Relationship means one of the four conditions below is met to define the DoS attacking activity.
- It is supposed to be DoS Attacking when broadcast packet per second is greater than its setting value or multicast packet per second is greater than its setting value. Both the setting values are an integer between 10 and 500 and 100 is set by default.
- It is supposed to be DoS Attacking when the ratio of sent packets to received packets is greater than its setting value and sent TCP SYN packet per second is greater than its setting value. The first setting value is an integer between 1 and 5 and 3 is set by default. The second value is an integer between 3 and 200, and 50 is set by default.
- It is supposed to be DoS Attacking when the ratio of sent packets to received packets is greater than its setting value and sent bytes per second is greater than its setting value. The first setting value is an integer between 1 and 5 and 3 is set by default. The second value is an integer between 1 and 100, and 10 is set by default.
- It is supposed to be DoS Attacking when the ratio of sent packets to received packets is greater than its setting value and sent packet per second is greater than its setting value. The first setting value is an integer between 1 and 5 and 3 is set by default. The second value is an integer between 100 and 1,000, and 500 is set by default.
DoS Attacked settings
The DoS attacked analysis detects the hosts which are under DoS attack and the settings part appears as follows:
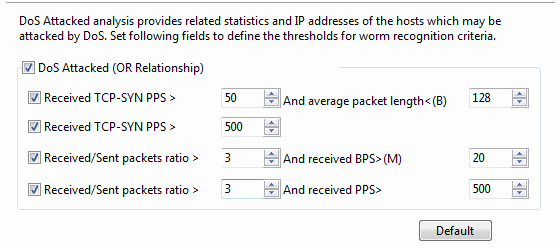
- DoS Attacked: Enables DoS attacked analysis, or else there will be no item to show on the DoS Attacked view. OR Relationship means one of the four conditions below is met to define the DoS attacked activity.
- It is supposed to be DoS Attacked when received TCP SYN packet per second is greater than its setting value and the average packet length is less than its setting value. The first setting value is an integer between 5 and 500 and 50 is set by default. The second setting value is an integer between 64 and 1518 and 128 is set by default.
- It is supposed to be DoS Attacked when received TCP SYN packet per second is greater than its setting value. The setting value is an integer between 5 and 1000, and 500 is set by default.
- It is supposed to be DoS Attacked when the ratio of received packets to sent packets is greater than its setting value and the received bytes per second is greater than its setting value. The first setting value is an integer between 1 and 5 and 3 is set by default. The second setting value is an integer between 1 and 100, and 20 is set by default.
- It is supposed to be DoS Attacked when the ratio of received packets to sent packets is greater than its setting value and the received packets per second is greater than its setting value. The first setting value is an integer between 1 and 5 and 3 is set by default. The second setting value is an integer between 50 and 1000, and 500 is set by default.
Default: Resets the setting of that type of security analysis to default.






