Colasoft Capsa is able to capture the important information unencrypted in LAN, such as email message, FTP transfers and HTTP requests. In other words, however, those information which can be captured is supposed to be unsafe.
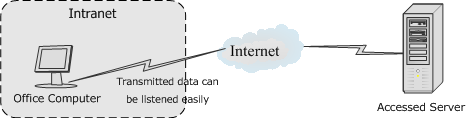
As shown in the figure below, in a common network data are transmitted without protection, important information would be listened easily if you meet with network attack.
In order to protect the important data transmitted over LAN, you may use the “Stunnel” tool to encrypt your data.
Stunnel (http://www.stunnel.org/) is a free program that allows you to encrypt arbitrary TCP connections inside SSL (Secure Sockets Layer) available on both Unix and Windows. Stunnel can allow you to secure non-SSL aware daemons and protocols (like POP, IMAP, LDAP, etc) by having Stunnel provide the encryption, requiring no changes to the daemon's code.
Stunnel program takes the Client/Server pattern – transmitting to a designated server side for decrypt after encrypting data on the client side, and then retransmitting to the destination server. You just need to install the server side program on a server outside your LAN, the data should be safe in the process of encryption transmission in LAN.
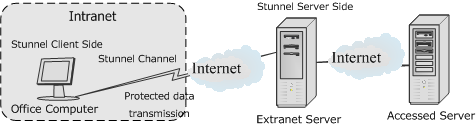
Processes
Stunnel is a free program. The following will introduce how to use this tool to encrypt data.
- Download the client side program (http://www.colasoft.com/download/products/stunnelclient.zip) and then unzip to the local category C:\Program Files;
- Download the server side program (http://www.colasoft.com/download/products/stunnelserver.zip) and then unzip to a server on extranet;
- Configure the file stunnel.conf respectively;
- Change the network connection configuration of corresponding application on local;
- Run stunnel.-4.04.exe respectively.
After configuration, you may create a shortcut of the .exe file in Start Menu to run the program automatically at every boot
Note: It is required to have a server with management authorization on extranet to run the Server program.
It also has a requirement on the bandwidth speed of the server because the encrypted data need to be decrypted via the server side.
Stunnel Configuration
Both the client side and server side contain the configuration file stunnel.conf, the format is as below:
|
stunnel.conf of client side |
stunnel.conf of server side |
|
# Use it for client mode
client = yes
#Client-level configuration
[name of application service]
accept = local IP: destination port
connect =server side IP: designated port |
# Use it for server mode
client = no
# server-level configuration
[name of application service]
accept = designated port
connect = destination server IP: destination port |
Stunnel.conf configuration is comparatively simple, the following are some common application configurations.
Examples:
In these configurations, the client side is on the local with IP 127.0.0.1; the server side is on an extranet server with IP 202.151.90.28.
Encrypted email transmission requires protecting the both process of sending and reception, so you need to encrypt the transmission method of POP3 and SMTP.
Suppose that you have a mail box xxx@colasoft.com and the server IP is 202.108.44.153, the configuration is as follows:
|
stunnel.conf of client side |
stunnel.conf of server side |
|
[smtp.colasoft.com]
accept = 127.0.0.1:25
connect = 202.151.90.28:125
[pop3.colasoft.com]
accept = 127.0.0.1:110
connect = 202.151.90.28:1110 |
[smtp.colasoft.com]
accept = 125
connect = 202.108.44.170:25
[pop3.colasoft.com]
accept = 1110
connect = 202.108.44.153:110 |
If there are multiple email transmissions to be encrypted, you need to add the corresponding configurations of POP3 and SMTP.
When finish the configuration, you also need to match the client side to it:
sending email address: change to 127.0.0.1
port number: change to 125
recipient email address: change to 127.0.0.1
port number: change to 1110
FTP transmits files in plain text, but with Stunnel the FTP transmission also can be safe. What you need to do is just append the following configuration information to the above stunnel.conf content:
|
FTP configuration of client side |
FTP configuration of server side |
|
#Client-level configuration
[ftp.net130.com]
accept = 127.0.0.1:21
connect = 202.151.90.28:121 |
#Server-level configuration
[ftp.net130.com]
accept = 121
connect = 218.7.9.73:21 |
FTP software also needs corresponding changes:
remote address: change to 127.0.0.1
port number: change to 121
It is impossible for us to encrypt all web accesses because of the large amount; however, as for some important accesses, you can use Stunnel to protect the accessed contents from being listened.
For example, if you would like to visit the site www.cnn.com, its IP is 64.236.24.12; the HTTP configuration can be set as below:
|
HTTP configuration of client side |
HTTP configuration of server side |
|
#Client-level configuration
[www.cnn.com]
accept = 127.0.0.1:80
connect = 202.151.90.28:8080 |
#Server-level configuration
[www.cnn.com]
accept = 8080
connect = 64.236.24.12:80 |
|

