How to Find DNS Amplification Attacked Server
Many network service abnormitis are often caused by Cyber-attacks, but there are many reasons for the abnormitis. How to analyze and locate the reasons is the key to solving the problem. A DNS amplification attack is a DoS attack. The attacker uses a large number of controlled hosts in the botnet to pretend to be the attacked host. And it continuously sends a large number of DNS requests to multiple DNS servers that allow recursive queries at a specific point in time, forcing servers to provide response services. A large amount of response data amplified by the DNS server is sent to the attacked host to form attack traffic, which causes it to fail to provide normal service or even paralysis.
Problem Description
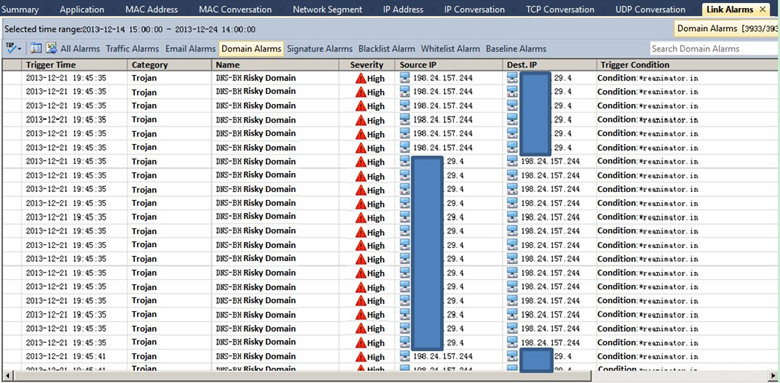
XX.XX.29.4 is a DNS server for a large industry client and this server needs to provide DNS services externally. Recently, the client’s network was congested, and the operation and maintenance department found that a large number of alarms were triggered in the Domain Alarm after deploying the Colasoft nChronos system.
Analysis Procedure
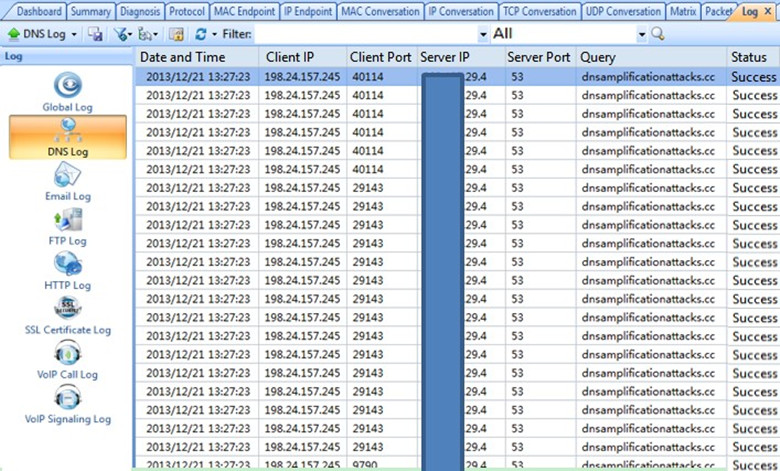
IP address “198.24.157.245” sent a large number of DNS requests to the XX.XX.29.4 server in a short period of time, the requested domain name is dnsamplicationattacks.cc.
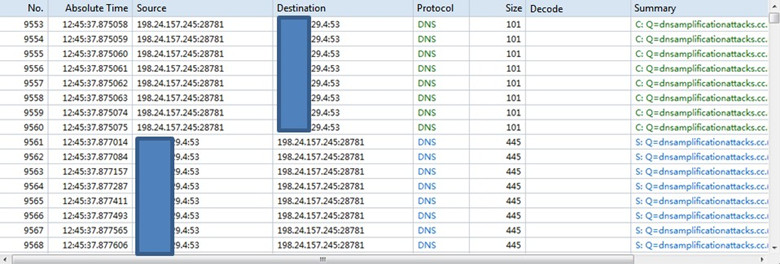
The request packet sent by “198.24.157.245” is 101 bytes, and the response packet returned by the DNS server is 445 bytes, which amplifies the traffic by 4.4 times.
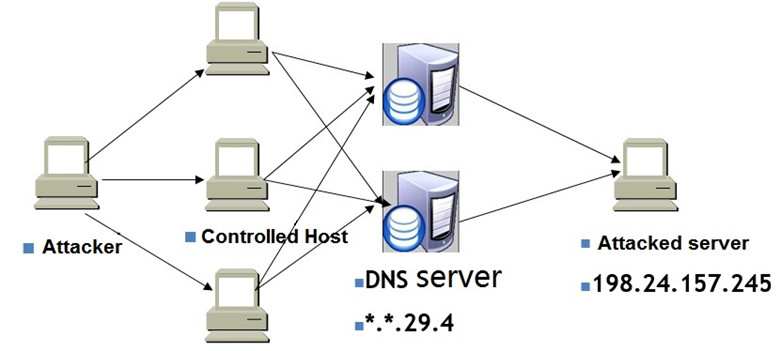
The attacker uses a large number of controlled hosts to send DNS requests to multiple DNS servers. However, the source IP address in the DNS request is forged as the IP address which is being attacked (in this case, the IP address “198.24.157.245” is being attacked), and the DNS server returns the query result to the IP address “198.24.157.245”. Usually, the response packet will be several times or even tens of times larger than the request packet (4.4 times in this example), resulting in a traffic amplification attack on the IP address “198.24.157.245”. In this case, the client's DNS server is involved as an agent to implement this DNS amplification attack. The attack process is shown in the following figure.
Analysis Conclusion
The attacker uses a large number of controlled hosts to send plenty of DNS requests to the DNS server (XX.XX.29.4) in a short period of time. The DNS response packet will be 4.4 times larger than the request packet, causing large traffic to be sent to the forged source IP address (198.24.157.245), forming a DoS attack on this IP address.
- We suggest our client:
- Increase link bandwidth;
- Close recursive query of DNS server;
- Once a large-scale DNS amplification attack occurs, you can immediately contact the ISP to filter the attack on the upstream router (ISP network).
nChronos Value
Hackers often use the characteristics of the DNS server as an attacking amplifier. They can rely on botnets to launch attacks, creating huge attack traffic, and they are always stealthy. However, in this case, we can see that the network traffic analysis technology can find out cyber-attack behavior easily and achieve the effect of visualizing the cyber-attack. And through the packet decoding, we are able to analyze the attack method of attackers clearly. Using network traffic analysis technology, through the depth analysis of layer 2 to layer 7, accurate decoding, detailed statistical data, to protect the customer's information system and network security.